5 quick wins for AI in identity and access management
After 30 years in cybersecurity, I’ve seen countless technologies promise to be the next silver bullet. Most aren’t. But today, we’re facing a challenge where a new approach isn’t just an option - it’s a necessity.
The challenge is Identity and Access Management (IAM). Our enterprises are no longer fortresses; they are hyper-connected ecosystems where identity is the last true perimeter. The sheer volume and complexity of access decisions have surpassed our teams' capacity to govern them effectively, leading to very real risks like “privilege creep” and “certification fatigue.”
And here’s the good news: we don’t need a multi-year, monolithic project to start winning back control. We can get immediate, practical value by applying AI - specifically generative AI - to our most pressing IAM challenges today. Before we talk about grand strategy, let’s talk about quick wins.
Here are a few pragmatic use cases where your teams can start leveraging AI right now, often with little more than the tools they already have.
5 Pragmatic use cases for AI in IAM
1. AI-powered access recertification
The Problem
The quarterly access review process is broken. It creates “certification fatigue,” where managers, overwhelmed with spreadsheets, rubber-stamp approvals, turning a critical security control into a meaningless compliance drill.
Generative AI Quick Start
A manager can manually export a user's list of permissions and a similar list from 3-4 of their peers. By pasting this data into a generative AI tool like Manus or Copilot and asking, "Compare this user's access to their peers and identify any permissions that are unique or high-risk outliers," they can get an instant, high-quality first-pass analysis. The value of this outlier analysis is immediate risk prioritization. It allows a manager to instantly see which access rights are unusual for a given role - representing potential privilege creep or misconfiguration - and focus their limited review time on these specific, high-risk items instead of a massive list of routine permissions.
The Long-Term Advantage
This manual quick start paves the road for full automation. The next step is to ingest user entitlement and activity logs into an AI engine that establishes peer group and usage baselines automatically. It then generates a risk-prioritized dashboard for managers with clear recommendations, automating the approval and revocation workflow. The system learns from manager decisions to make the next cycle even smarter.
2. Remediating excessive permissions
The Problem
“Privilege creep” is a natural entropy that leaves a massive attack surface. Users constantly accumulate more access than they need, and manually right-sizing these permissions is a near-impossible, continuous task.
Generative AI quick start
An analyst can export a user's assigned IAM policy (in JSON format) and a log of their actual API activity over the last 90 days. They can then prompt an AI assistant: "Here is a user's granted IAM policy and their actual usage. Generate a new, right-sized policy that only includes the permissions they have actually used."
The long-term advantage
This manual process of generating right-sized policies becomes the blueprint for an automated Principle of Least Privilege (PoLP) engine. The AI can be trained to continuously analyze the gap between granted and used permissions, automatically suggesting policy adjustments that can be applied with a single click, perpetually optimizing your access posture.
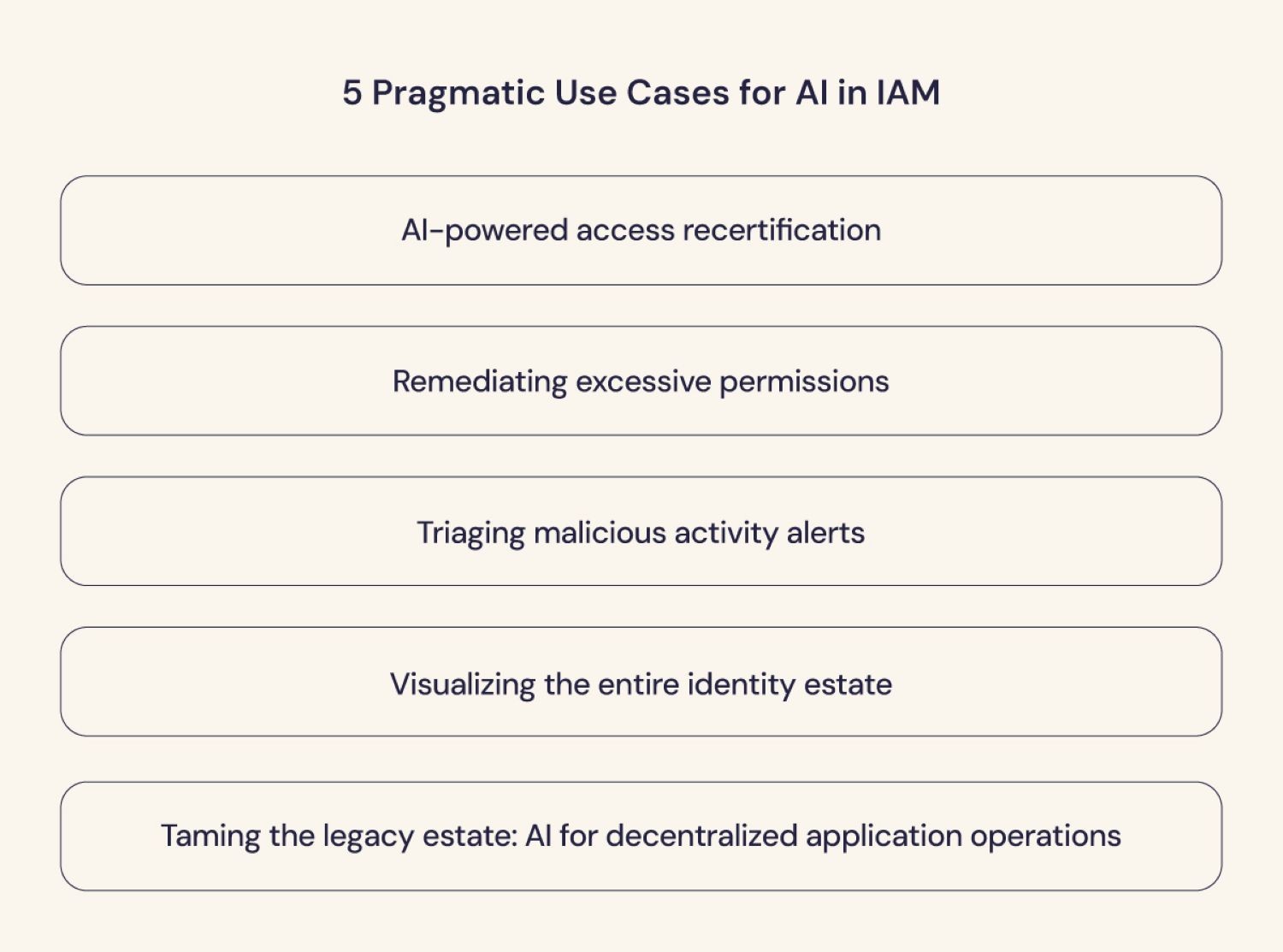
3. Triaging malicious activity alerts
The problem
Our Security Operations Center (SOC) is drowning in a sea of low-fidelity alerts, leading to analyst burnout and the high risk of missing a genuine, sophisticated attack. The signal-to-noise ratio is dangerously low.
Generative AI quick start
A SOC analyst can copy a raw, cryptic alert from the SIEM and paste it into a chat interface with the prompt: "This user just triggered this alert. Here is their role and login history. Given the recent uptick of attackers using compromised credentials in the retail sector, is this likely a false positive, or does it align with known attacker TTPs? What are the top 3 questions I should ask to verify?" This enriches the alert with both user context and external threat context, leading to a much more accurate initial assessment.
The long-term advantage
This manual enrichment process trains the AI. Eventually, the system can automatically ingest security alerts, correlate them with identity behavior and threat intelligence, and resolve the vast majority of false positives on its own, escalating only the critical few high-fidelity incidents to human analysts.
4. Visualizing the entire identity estate
The problem
Our access landscape is an opaque maze. It’s nearly impossible to answer a simple question like “Who can access our customer data?” because permissions are nested across a complex web of hybrid systems.
Generative AI quick start
An investigator can manually gather a user's group memberships and role assignments and ask the AI: "This user is in the 'Project-X-Admins' and 'EU-Finance-Auditors' groups. The second group has access to the 'EU-Customer-Data' application. Generate a Mermaid-syntax diagram showing the potential access path from the user to customer data." The value of this visual diagram is making the invisible visible. It transforms a complex, abstract list of groups into a clear, traceable map, allowing an investigator to instantly understand the "blast radius" of a compromised account or identify non-obvious, high-risk access pathways that are impossible to spot in text-based lists.
The Long-term advantage
This manual diagram generation is the first step toward building a dynamic, comprehensive identity graph. By connecting the AI to all identity stores (Active Directory, cloud IAM, HR systems), it can create a living, navigable 3D map of the entire identity estate, which becomes the foundational data layer for all other advanced AI-IAM initiatives.
5. Taming the legacy estate: AI for decentralized application operations
The problem
Our application portfolio includes a significant number of legacy, non-federated applications. These systems are "decentralized" not by modern design, but by default—each has its own siloed user store and arcane procedures. Every user management request is a bespoke, manual task that relies on tribal knowledge.
Generative AI quick start
An IT support person gets a ticket to add a user to "FinApp-v3," a legacy accounting system from a 15-year-old acquisition. Instead of searching for outdated documentation or interrupting a senior engineer, they prompt an AI assistant: "Generate a step-by-step plan, with exact menu navigation and field entries, to add a new user with 'Auditor' permissions to the FinApp-v3 system." This provides an instant, accurate runbook, turning a 45-minute research task into a 5-minute execution.
The Long-term advantage
This AI-generated runbook becomes the training data for an AI-orchestrated Robotic Process Automation (RPA) bot. The AI generates the plan, and the RPA bot executes the UI clicks and data entry, fully automating the task and taming the legacy sprawl without costly custom integration projects.
From quick wins to a transformative strategy
These 5 use cases demonstrate that we can start small and deliver immediate value. But the real power comes from connecting these individual quick wins into a cohesive, long-term strategy. How do we build the paved road from these initial tactical victories to a full-scale transformation of our IAM program? The journey is an iterative one, where each phase builds on the last, creating a continuous feedback loop that drives evolution.
This journey can be broken down into 4 key phases:
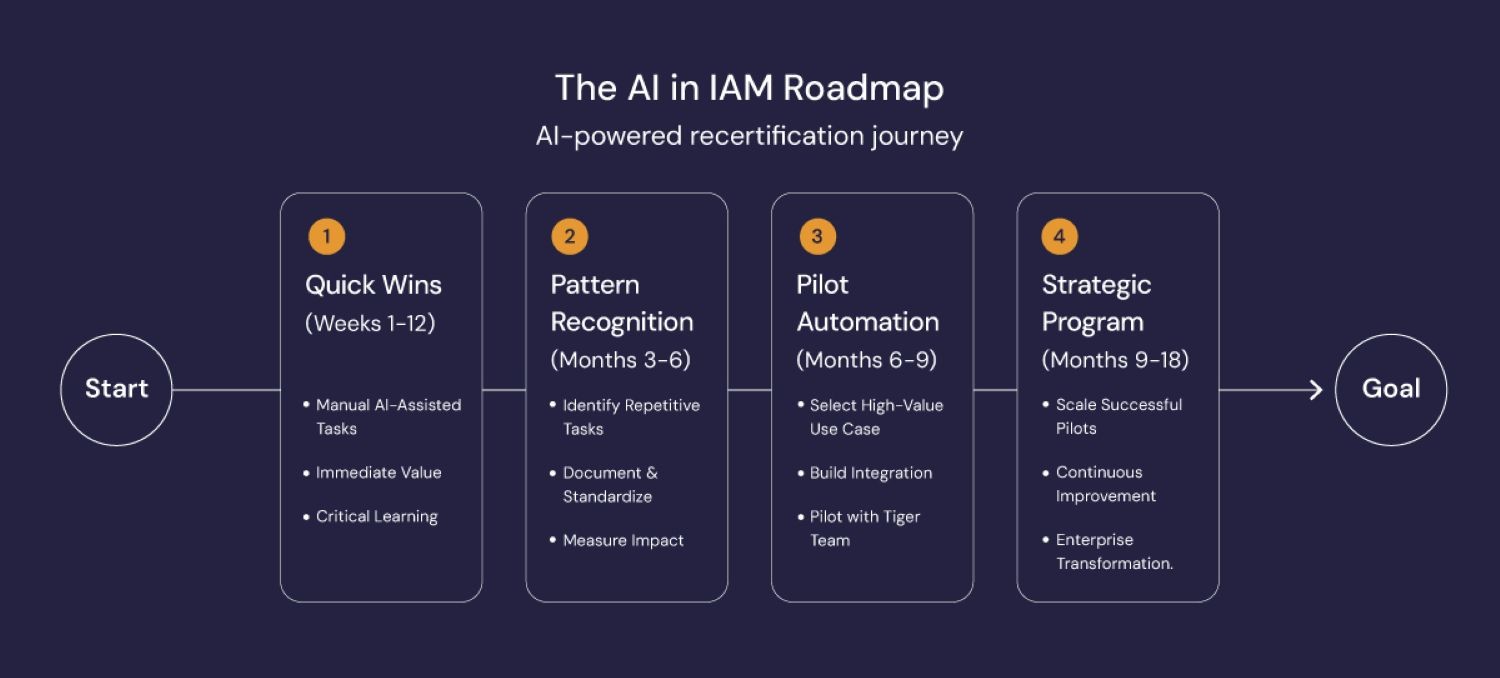
Phase 1: Quick Wins (Weeks 1-12)
This is where we start. Our teams use generative AI for manual, ad-hoc tasks. The focus is on immediate value and, most importantly, learning. We discover which use cases are most valuable, what data is required, and where the biggest organizational pain points are.
Phase 2: Pattern Recognition (Months 3-6)
As teams use these tools, patterns emerge. We identify the most common and repetitive tasks and begin to standardize them by creating prompt libraries and data templates. We also start measuring the impact in terms of hours saved and errors reduced.
Phase 3: Pilot Automation (Months 6-9)
Armed with data from Phase 2, we select the highest-value use case for a formal automation pilot. We build the necessary integrations to automate the data flow and test the solution with a small, dedicated tiger team. This is our first step into true automation.
Phase 4: Strategic Program (Months 9-18)
Once the pilot is successful, we scale it. This is where we move from a project to a program. We roll out the solution to all users, begin looking for the next use case to automate, and establish a formal AI Center of Excellence. The AI models continuously learn from new data and user decisions, creating a virtuous cycle of improvement.
This phased approach, built on a foundation of quick wins, is how we can build a truly strategic, AI-powered IAM program from the ground up. It’s a pragmatic and sustainable path to transformation.
Scale AI in identity and access management
Track 1: Empowering Our People (The Quick Wins We Just Covered)
This is the foundation. We encourage and equip our teams to use generative AI as a “force multiplier” in their daily work. This builds an AI-native culture from the ground up and delivers immediate efficiency gains.
Track 2: Building a Roadmap for Strategic Automation
In parallel, we use the insights from our quick wins to inform a more strategic roadmap.
This involves:
Prioritizing for Impact: We need to decide which of these use cases to pursue for full automation first. To do this, we can apply a structured framework that balances financial impact, implementation complexity, organizational readiness, and strategic value. A hypothetical analysis suggests that AI-Powered Recertification is often the ideal starting point, as it sits squarely in the “Quick Wins” quadrant of high value and low complexity.
Forming a Small Team of Evangelists: A small, cross-functional “tiger team” can champion the vision, pilot the first fully automated use case, and become the center of excellence for AI in IAM.
Developing an Iterative Roadmap: We can use a universal value chain framework to ensure every project, from manual quick win to full automation, is structured, systematic, and focused on delivering measurable outcomes.
A thoughtful path forward
This analysis aligns with a key lesson from my 30 years of experience: the most sustainable path to success often begins with a high-impact, low-complexity win that solves a real, acknowledged pain point. Starting with these tangible, pragmatic use cases allows us to build momentum, demonstrate value to the business, and lay the cultural and technical groundwork for a truly intelligent and resilient identity security program.
I’m sharing this perspective because I believe this is a sound way to drive this change, and I’m interested in hearing how my fellow technology leaders are thinking about these same challenges. What has your experience taught you?
Erik is an cybersecurity executive and advisor with over 20 years of experience leading cloud security, identity, and enterprise risk transformation. Formerly SVP – Cloud Security & Architecture at M&T Bank, he has also held leadership roles at GitHub, Veracode, and ACV Auctions. Erik advises emerging cybersecurity innovators, including Cyera, Legit Security, Cyberstarts, and Permiso Security, and through his firm, Pragmatic Strategies, helps organizations turn complex security challenges into actionable strategy and measurable results.