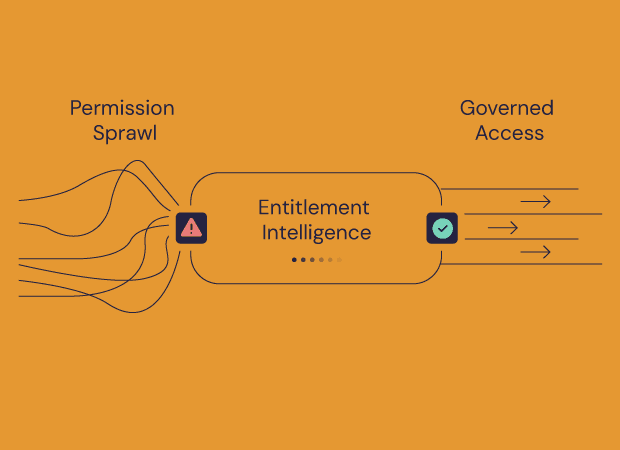
Modernizing the identity stack with entitlement intelligence
This Software Analyst Cyber Research (SACR) analyst report explores how entitlement intelligence enables AI-native identity governance for modern enterprises.
Learn how leading organizations are closing the gap between identity visibility and control, reducing risk while maintaining agility in complex cloud environments.
How entitlement intelligence unifies fragmented identity data to provide complete visibility across your IAM stack
The framework for transitioning from manual access reviews to AI-driven, automated identity governance
Key capabilities that enable enterprise security teams to detect and remediate identity risks at scale
01
The identity governance gap
Why traditional IAM tools provide visibility without control, leaving enterprises vulnerable to access-related risks.
02
Entitlement intelligence
How unified identity data creates the foundation for AI-native governance and automated remediation.
03
From visibility to governance
A framework for transforming fragmented identity insights into actionable, automated security controls.
04
The future of IAM
Key capabilities and strategic considerations for building an AI-native identity governance stack.
Written by leading IAM analysts, this report provides a strategic roadmap for CISOs and security leaders navigating the shift to AI-native identity infrastructure. Packed with real-world implementation guidance and enterprise use cases for entitlement intelligence adoption.
Resource type - Analyst report
Skill level - Intermediate
Product focus - Identity governance and entitlement intelligence