Why entitlement intelligence is the missing layer in IAM security
After 20 years in cybersecurity, I thought I understood every IAM challenge.
But recently, Software Analyst Cyber Research (SACR), the analyst firm led by Francis Odum, validated what I've been seeing in the field:
The biggest security gap in identity isn’t authentication – it's authorization.
It’s not who logs in, but what they can do once they’re inside.
The report from SACR, "Modernizing the Identity Stack: From Visibility to Governance Through Entitlement Intelligence," captures this shift in stark terms.
While organizations have invested heavily in MFA, SSO, and passwordless authentication, attackers continue to succeed by exploiting excessive privileges, stale entitlements, and forgotten service accounts.
The pattern behind credential-based breaches
The data is clear: credential compromise remains the dominant attack vector across every major threat intelligence source.
According to Verizon's 2025 Data Breach Investigations Report, stolen credentials account for 31% of breaches. Attackers don't need to crack passwords - they simply inherit legitimate access and move laterally through over-privileged accounts.
IBM's Cost of a Data Breach Report reinforces this pattern. Breach costs averaged $4.44 million globally in 2025, with US breaches reaching $10.22 million. Beyond the costs, incidents involving compromised credentials take 8-10 months to identify and contain, and 97% of AI-related incidents lacked proper access controls.
The common thread? Authorization failures and permission sprawl.
We've spent years perfecting the front door while leaving every room unlocked.
The authorization sprawl problem
In modern enterprises, we’re seeing:
Hundreds of SaaS applications
Complex on-premises and custom-built systems
Multi-cloud infrastructure sprawl
Exploding populations of machine identities
Emerging AI agents accessing enterprise resources
A typical enterprise now operates across 200+ SaaS applications, multiple cloud providers, and thousands of service accounts. Each platform has its own authorization model - AWS IAM policies, Azure RBAC, Salesforce profiles and permission sets, Google Workspace roles.
The permutations are endless, and the relationships between them are opaque.
Traditional Identity Governance and Administration (IGA) tools were built for a simpler era. They manage workflows and orchestrate approvals, but they lack semantic understanding of what granted access actually enables.
Entitlement intelligence is the missing authorization layer that’s needed to understand not just who has access to what - but whether they should, what it enables them to do, and how to remediate misalignments without breaking business workflows.
The fragmentation undermines the core value proposition of governance. When IGA platforms lack normalized and contextual views of entitlements, access certifications become superficial, role engineering becomes unmanageable, and policy enforcement becomes inconsistent.
Organizations compensate through manual spreadsheet mapping and custom connectors - approaches that increase cost without establishing durable visibility.
Access reviews have turned into checkbox exercises
Every CISO reading this is familiar with the quarterly access review ritual.
Managers receive spreadsheets with hundreds of technical permissions, lacking business context, usage data, or risk indicators. Unsurprisingly, these reviews result in near-universal approval, creating "rubber-stamping exercises" that fail to reduce actual risk.
Research cited in the SACR report shows 58% of identity leaders say their access reviews are ineffective. When 42% of reviewers lack the context to make informed decisions, we're not doing governance - we're performing compliance theater.
The problem compounds over time.
Entitlements, once granted, persist indefinitely. Privilege creep becomes the default state. Organizations are left with dormant admin accounts, forgotten service account tokens, and excessive permissions that expand the blast radius of any compromise.
Why remediation bottlenecks matter more than detection
Even when organizations successfully identify over-entitled users or toxic permission combinations, remediation often stalls.
This is what I've seen firsthand:
Most IGA tools were designed to orchestrate approvals, not to implement precise, dependency-aware entitlement changes across SaaS, cloud, and legacy systems.
Remediation commonly devolves into IT tickets requiring coordination across identity teams, application owners, and security staff. Each change must be risk-assessed, tested, approved, and sequenced correctly - especially in applications where permissions are deeply intertwined with business workflows.
This operational friction creates persistent remediation backlogs, and many organizations can't remediate fast enough due to coordination and tooling limitations. These excessive privileges remain in place long after they're identified, creating sustained risk windows that attackers can exploit.
What entitlement intelligence actually means
Entitlement intelligence serves as the authorization backbone of the identity stack - it's more foundational than visibility tools or posture management platforms. It's the semantic layer that makes entitlement meaning operational.
Traditional approaches treat entitlements as strings or role assignments – yet specialized LLMs trained on enterprise entitlement patterns can decode what these permissions actually mean - understanding their business impact, not just their labels.
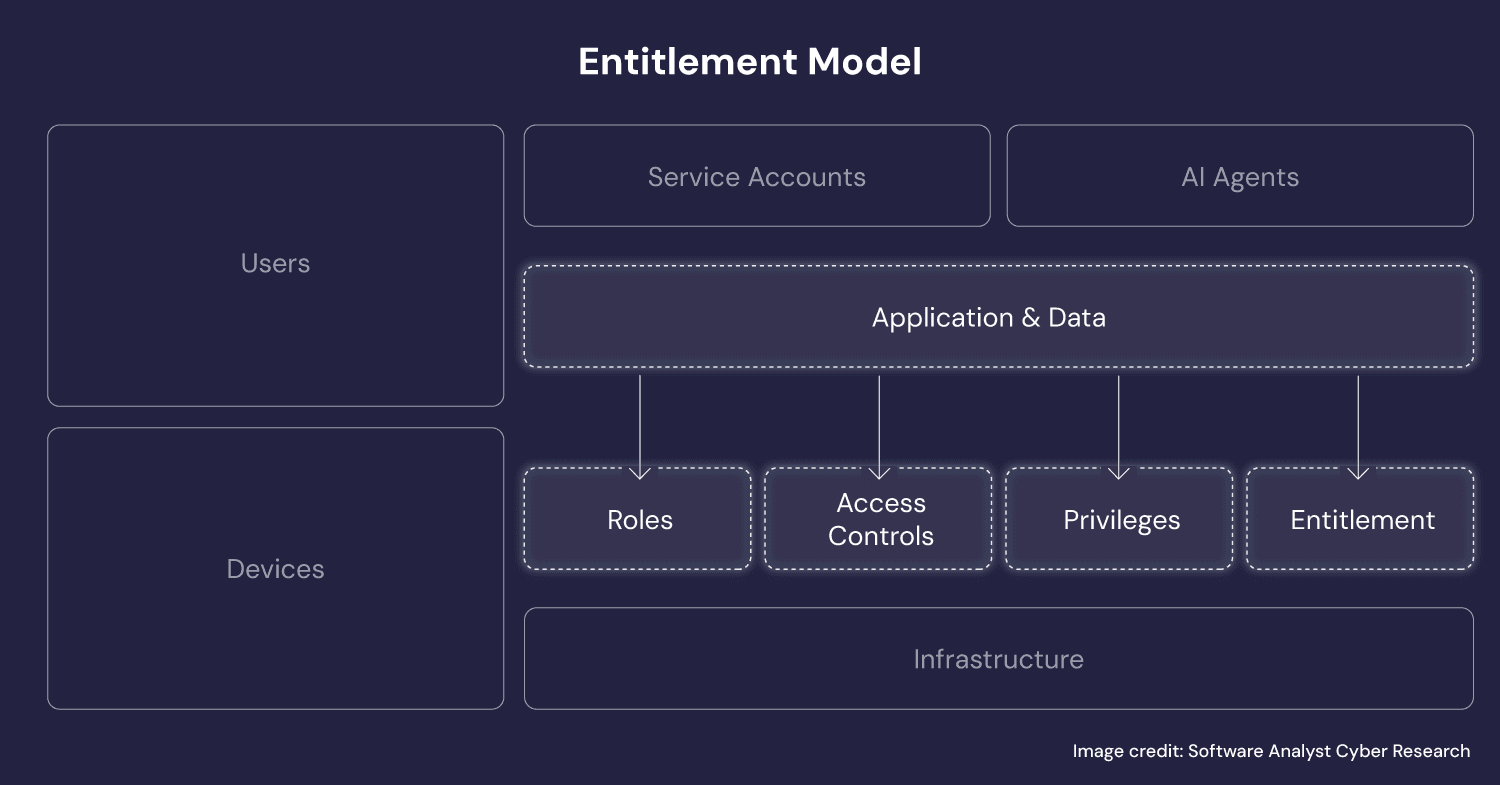
The SACR report identifies this as a critical differentiator: proprietary models for semantic normalization at scale. Where legacy IGA systems depend on human-defined roles and brittle connectors, the future belongs to platforms that can infer entitlement structure automatically across SaaS and on-premises systems.
The shift to continuous, intelligent governance
After years of watching these cycles repeat, I'm convinced quarterly certification campaigns and user access reviews need to be fundamentally augmented to make the process both more efficient but especially more meaningful. Modern identity governance must shift toward risk-driven, continuous review models where reviewer context and decision quality matter more than mechanical compliance.
This means user access reviews augmented with peer baselines, entitlement usage patterns, risk classifications, and policy explanations.
The objective isn't to review everything on a fixed schedule, but to focus governance efforts where risk is highest and change is occurring.
At Opti, we've seen this transformation firsthand. When reviewers understand what an entitlement actually grants, who else has similar access, and how usage patterns compare, they make substantive decisions instead of clicking "approve all."
Our risk mitigation engine provides this context - turning access reviews from compliance exercises into meaningful security controls.
Why non-human identities can’t be ignored
Non-human identities (NHIs) represent the fastest-growing attack surface in identity governance. Service accounts, API keys, and emerging AI agents are proliferating faster than human identities, yet most organizations lack basic visibility into their entitlements.
The risk of waiting is real.
We're seeing it with our customers - organizations that postponed dealing with service account sprawl are now scrambling as AI agents multiply their machine identity footprint by orders of magnitude.
Opti’s lifecycle management capabilities extend to both human and NHIs, providing the governance layer organizations need as automation scales.
5 steps CISOs should take to modernize identity governance
Based on what we're seeing in the market and what the research validates, here are steps that modern CISOs should take:
Add entitlement intelligence
Treat entitlement intelligence as foundational infrastructure - Authorization sprawl is the primary identity risk. Add the semantic understanding layer beneath your existing IAM and IGA tools.Automate the security workflow
Identity security can't be a manual investigation every time. Build systems that continuously find identity issues, assess their risk level, prioritize what matters most, and automate remediation wherever possible. The faster you move from detection to resolution, the smaller your risk window.Grant least privilege from day one
Provision access based on actual role requirements, not inflated templates. During onboarding, grant only the permissions employees need. When they move roles, automatically recalibrate their access - add what's needed, remove what's not. This prevents the privilege accumulation that turns every account into a lateral movement opportunity.Move from periodic reviews to continuous governance
Replace quarterly access reviews with continuous, risk-driven models. Provide reviewers with context—what permissions enable, usage patterns, peer baselines—so governance becomes a real control, not compliance theater.Prioritize remediation over detection
Finding identity issues matters less than fixing them. Visibility without action is security theater—the gap between detection and remediation determines your actual risk. Build systems that close that gap fast.
Why authorization security matters now
The identity market solved authentication over the past decade.
Now, we need the same investment in authorization. With Microsoft reporting 600 million identity attacks daily, attackers don't need to crack your MFA—they just inherit legitimate access and exploit permission sprawl.
Governance can't be a compliance checkbox anymore.
It needs to be intelligent, continuous, and operationally useful. Organizations that make this shift now - treating entitlement intelligence as foundational infrastructure - will be materially better positioned against the credential-based attacks dominating modern breaches.
We built Opti because after two decades in cybersecurity, I've seen what happens when the gap between authentication strength and authorization sprawl grows too wide.
Access the full
Barak, CEO and CO-founder of Opti, is a cybersecurity innovator with over 20 years of hands-on experience leading strategy, building products, and protecting critical infrastructures. He co-founded Indegy and served as its CEO until its acquisition by Tenable in 2019 where he served as VP. Earlier, he led product design at Stratoscale and managed large-scale cybersecurity projects in the Israel Defense Forces. Barak holds a B.Sc. in Computer Science and Mathematics and an MBA from Tel Aviv University.





